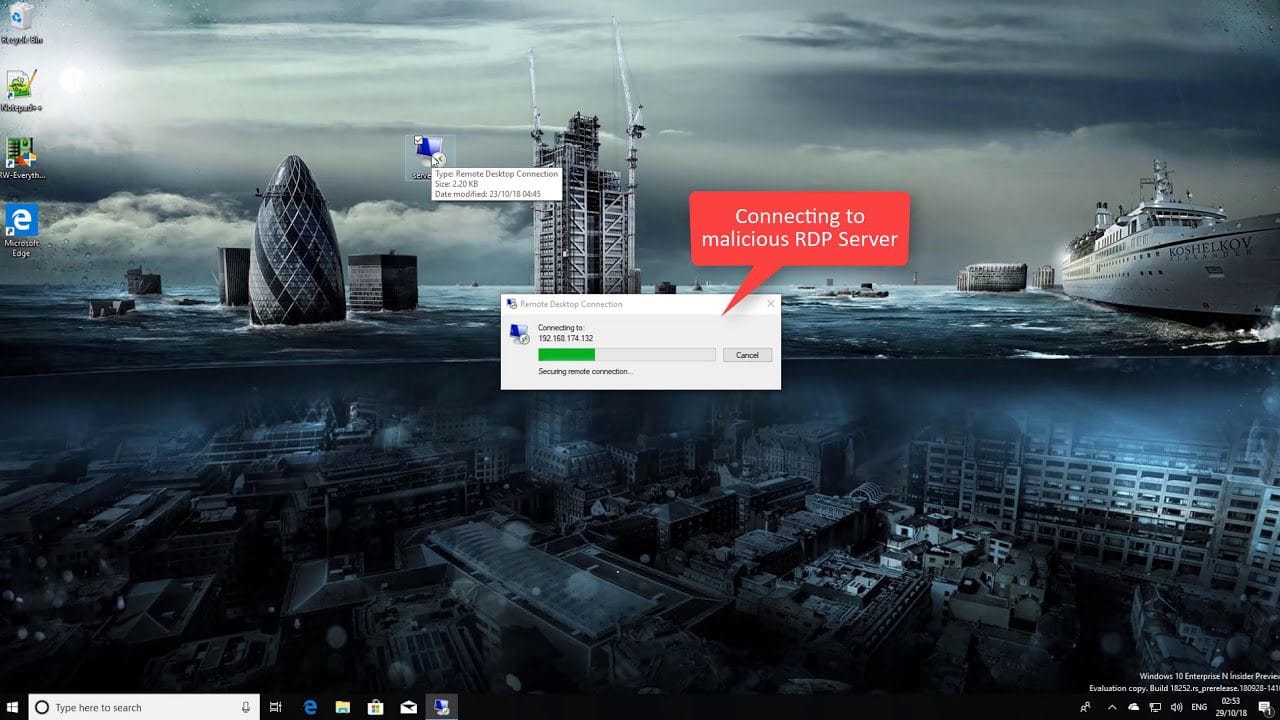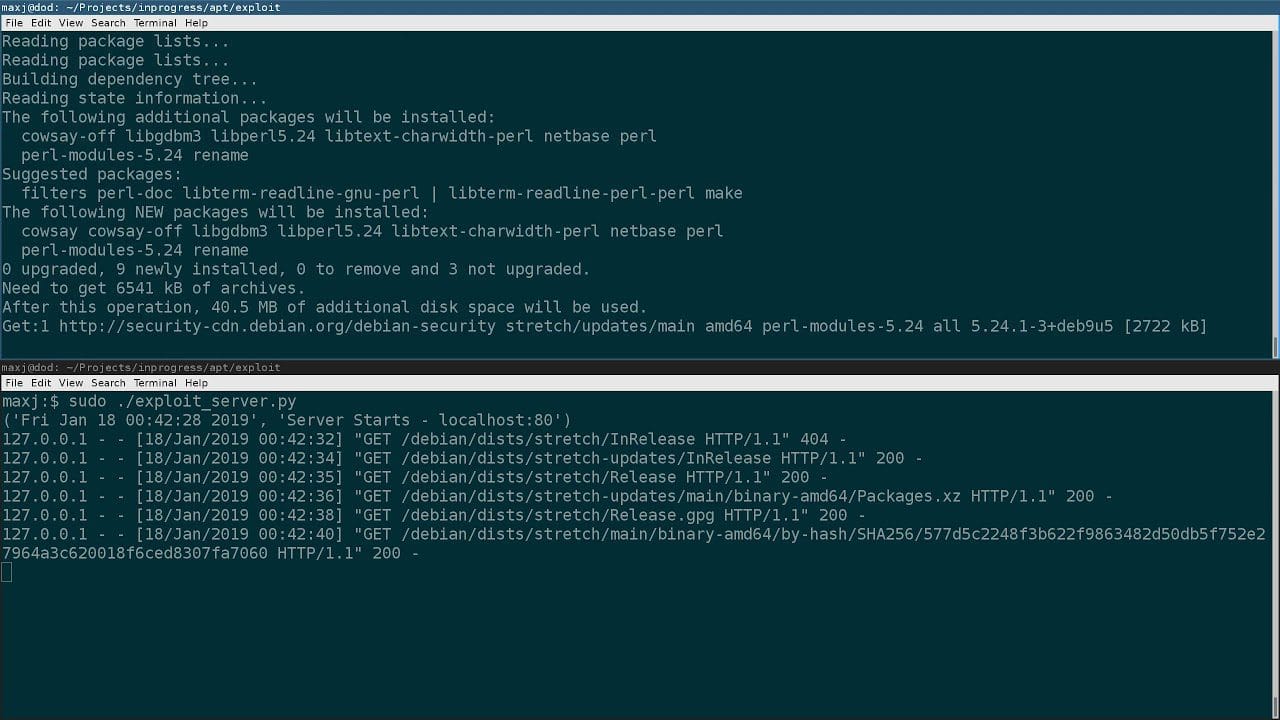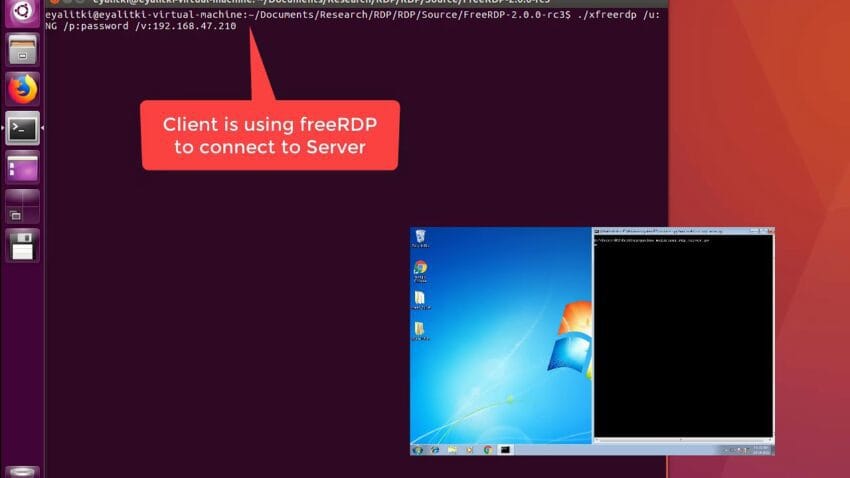
freerdp remote code execution attack via rdp A recently discovered vulnerability in FreeRDP has raised significant concerns regarding remote code execution via RDP connections.
freerdp remote code execution attack via rdp
Overview of FreeRDP
FreeRDP is an open-source implementation of the Remote Desktop Protocol (RDP), which allows users to connect to remote computers over a network. It is widely used in various environments, including corporate networks and personal setups, due to its flexibility and compatibility with multiple operating systems. The software is particularly popular among system administrators and IT professionals who require remote access to manage servers and workstations.
The Vulnerability
The vulnerability identified in FreeRDP allows for remote code execution (RCE), which means that an attacker can execute arbitrary code on a target machine without the user’s consent. This type of vulnerability is particularly dangerous because it can lead to unauthorized access, data theft, and potentially complete control over the affected system.
Technical Details
While specific technical details of the vulnerability have not been fully disclosed, it is understood that the flaw resides in the way FreeRDP handles certain RDP connection requests. Attackers can exploit this vulnerability by sending specially crafted RDP packets to a vulnerable FreeRDP client. Once the malicious packets are received, the vulnerability can be triggered, allowing the attacker to execute code on the victim’s machine.
Impact of the Vulnerability
The implications of this vulnerability are significant. Organizations that rely on FreeRDP for remote access may find themselves at risk of cyberattacks. An attacker could potentially gain access to sensitive information, install malware, or even take control of the system entirely. This could lead to data breaches, financial losses, and damage to an organization’s reputation.
Stakeholder Reactions
The discovery of this vulnerability has prompted reactions from various stakeholders, including cybersecurity experts, IT administrators, and users of FreeRDP. Many experts have urged organizations to take immediate action to mitigate the risks associated with this vulnerability.
Cybersecurity Experts
Cybersecurity experts have emphasized the importance of promptly applying security patches and updates. They recommend that organizations review their remote access policies and consider implementing additional security measures, such as multi-factor authentication and network segmentation, to reduce the risk of exploitation.
IT Administrators
IT administrators are particularly concerned about the potential impact on their systems. Many have begun assessing their use of FreeRDP and are evaluating whether to continue using the software or switch to alternative solutions. Some administrators have reported that they are increasing monitoring of their networks to detect any unusual activity that may indicate an attempted exploitation of the vulnerability.
Mitigation Strategies
To protect against the risks posed by this vulnerability, organizations should consider implementing several mitigation strategies.
Patch Management
One of the most critical steps is to ensure that all FreeRDP installations are updated to the latest version. The FreeRDP development team is expected to release patches that address this vulnerability, and organizations should prioritize applying these updates as soon as they become available.
Network Security Measures
Organizations should also review their network security measures. This includes implementing firewalls to restrict access to RDP services, using VPNs for remote connections, and employing intrusion detection systems to monitor for suspicious activity. By limiting exposure to the internet and ensuring that only authorized users can access RDP services, organizations can significantly reduce their risk.
User Education
Educating users about the risks associated with remote desktop connections is another vital strategy. Users should be trained to recognize phishing attempts and other tactics that attackers may use to exploit vulnerabilities. Regular training sessions can help ensure that users remain vigilant and aware of the potential threats.
Broader Context of RDP Vulnerabilities
This vulnerability in FreeRDP is part of a broader trend of RDP-related security issues. In recent years, RDP has been a popular target for cybercriminals, largely due to its widespread use and the potential for significant impact when exploited. High-profile attacks, such as ransomware incidents, have often involved the exploitation of RDP vulnerabilities.
Historical Perspective
Historically, RDP has faced scrutiny for its security flaws. Various vulnerabilities have been discovered in both proprietary and open-source implementations of the protocol. As remote work becomes increasingly common, the importance of securing RDP connections has never been more critical. Organizations must remain vigilant and proactive in addressing these vulnerabilities to protect their systems and data.
Conclusion
The recent discovery of a remote code execution vulnerability in FreeRDP serves as a stark reminder of the importance of cybersecurity in an increasingly connected world. As organizations continue to rely on remote access solutions, they must prioritize security and take proactive measures to mitigate risks. By staying informed about vulnerabilities, applying patches promptly, and implementing robust security measures, organizations can safeguard their systems against potential attacks.
In summary, the FreeRDP vulnerability highlights the ongoing challenges associated with remote desktop protocols. As cyber threats continue to evolve, organizations must adapt their security strategies to protect against emerging risks. The collaboration between cybersecurity experts, IT administrators, and users will be essential in creating a safer digital environment.
Source: Original report
Was this helpful?
Last Modified: September 8, 2025 at 6:32 pm
3 views