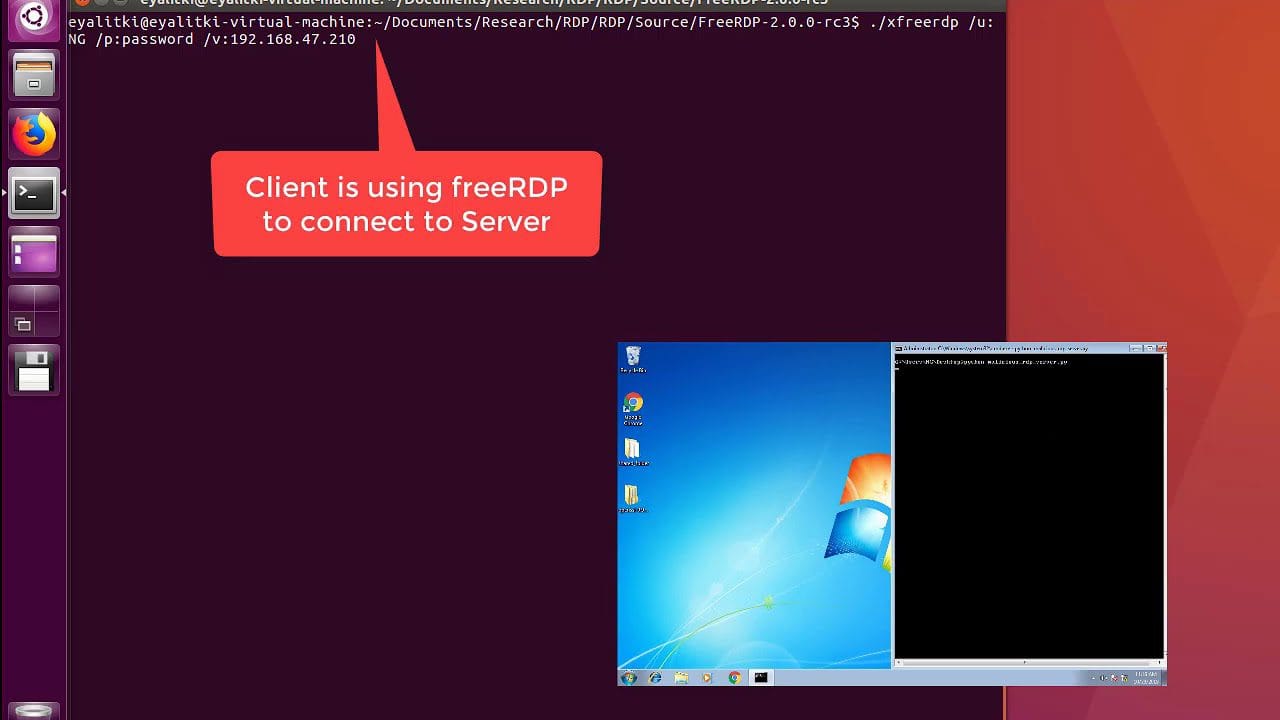
exploiting a remote desktop connection path traversal A recent security analysis has highlighted a significant vulnerability in the Remote Desktop Protocol (RDP) that could allow attackers to exploit a path traversal issue within the shared clipboard feature.
exploiting a remote desktop connection path traversal
Understanding Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft, enabling users to connect to another computer over a network connection. It is widely used in enterprise environments for remote management and support, allowing users to access their desktops and applications from virtually anywhere. RDP facilitates a seamless experience by allowing users to interact with remote systems as if they were physically present.
One of the key features of RDP is the shared clipboard, which allows users to copy and paste text and files between the local and remote systems. While this feature enhances usability, it also introduces security risks that can be exploited if not properly secured.
The Path Traversal Vulnerability
The recently identified path traversal vulnerability in RDP’s shared clipboard feature allows attackers to manipulate file paths in a way that can lead to unauthorized access to sensitive files on the remote system. Path traversal vulnerabilities occur when an application does not properly validate user input, allowing an attacker to access files and directories outside of the intended directory structure.
In the context of RDP, this vulnerability can be exploited by sending specially crafted data through the shared clipboard. An attacker could potentially gain access to files that should be restricted, leading to data breaches or unauthorized system access.
Mechanics of the Exploit
The exploit works by taking advantage of the way RDP handles clipboard data. When a user copies data to the clipboard, it can include file paths. If an attacker can manipulate this data, they can craft a path that points to sensitive files on the remote machine.
For instance, an attacker could use a relative path that navigates up the directory structure, bypassing security measures that are meant to restrict access to certain files. This could allow the attacker to read or even overwrite critical files, potentially compromising the integrity of the system.
Potential Impact of the Vulnerability
The implications of this vulnerability are significant, especially for organizations that rely heavily on RDP for remote access. If exploited, attackers could gain access to sensitive information, including personal data, financial records, and proprietary business information. This could lead to a range of consequences, including data breaches, financial loss, and reputational damage.
Moreover, the vulnerability could be used as a stepping stone for further attacks. Once an attacker gains access to a system, they may be able to deploy additional malware, escalate privileges, or move laterally within the network, increasing the overall risk to the organization.
Stakeholder Reactions
The discovery of this vulnerability has prompted reactions from various stakeholders in the cybersecurity community. Security researchers have expressed concern over the potential for widespread exploitation, particularly given the popularity of RDP in corporate environments. Many organizations have been urged to review their security practices and implement additional safeguards to mitigate the risks associated with this vulnerability.
Microsoft, as the developer of RDP, has been notified of the issue and is expected to release a patch to address the vulnerability. Organizations are advised to stay updated on security patches and apply them promptly to reduce their exposure to potential attacks.
Mitigation Strategies
To protect against the exploitation of this vulnerability, organizations should consider implementing several mitigation strategies:
- Update Software Regularly: Ensure that all systems are running the latest version of RDP and that security patches are applied as soon as they are released.
- Limit RDP Access: Restrict RDP access to only those users who absolutely need it. Use VPNs or other secure methods for remote access.
- Implement Network Segmentation: Segment networks to limit the potential impact of an exploit. This can help contain any breaches that may occur.
- Monitor Clipboard Activity: Implement monitoring solutions that can detect unusual clipboard activity, which may indicate an attempted exploit.
- Educate Users: Provide training for users on the risks associated with RDP and the importance of maintaining security best practices.
Conclusion
The path traversal vulnerability in RDP’s shared clipboard feature underscores the importance of vigilance in cybersecurity practices. As remote work becomes increasingly common, the reliance on RDP and similar technologies will likely continue to grow. Organizations must remain proactive in identifying and mitigating vulnerabilities to protect their sensitive data and maintain the integrity of their systems.
As the cybersecurity landscape evolves, it is crucial for stakeholders to collaborate and share information about emerging threats. By staying informed and implementing robust security measures, organizations can better safeguard their systems against potential exploits.
In summary, the exploitation of the RDP path traversal vulnerability poses a serious risk to organizations that utilize this protocol for remote access. By understanding the mechanics of the exploit and taking appropriate mitigation steps, organizations can significantly reduce their risk exposure and enhance their overall security posture.
Source: Original report
Was this helpful?
Last Modified: September 8, 2025 at 6:32 pm
2 views